So I've got a rather odd case here that showed up. I've never seen anything quite like it. It's a microSD card from an Android device. Suddenly the pictures all seemed corrupted to the user. The card and filesystem all seem normal, but the opening signature of all the jpgs and video files on the card look like this:
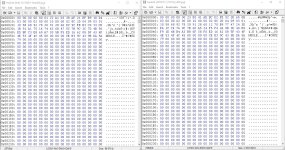
As you can see there is some variance in the opening signature, likely a checksum or key of sorts. But some elements such as the second line of 03 00 00 02 00 00 10 00 00 02 8C 2D 04 09 03 01 as well as the visible code "CONSOLE" are consistent. This is then followed by a few sectors of all zeros before random looking data begins (as you'd expect in a jpg or video).
Has anyone ever come across such an Android ransomware or have any idea which one this might actually be? There doesn't seem to be any ransom notes left behind anywhere.

As you can see there is some variance in the opening signature, likely a checksum or key of sorts. But some elements such as the second line of 03 00 00 02 00 00 10 00 00 02 8C 2D 04 09 03 01 as well as the visible code "CONSOLE" are consistent. This is then followed by a few sectors of all zeros before random looking data begins (as you'd expect in a jpg or video).
Has anyone ever come across such an Android ransomware or have any idea which one this might actually be? There doesn't seem to be any ransom notes left behind anywhere.
